Table of Content
- Overview
- Capabilities of Microsoft 365 Mobile Device Management
- Remotely Wipe a Mobile Device
- Summary
Overview
If you have a subscription to Microsoft 365 with a plan that includes the Mobile Device Management (MDM) capabilities, you have an excellent tool to secure your mobile devices. If you are like many businesses, you have a workforce that use mobile devices to check emails and conduct other work while at the office and on the go. Mobile devices such as iPhones, iPads, Android and Windows smartphone are commonly used in varying degrees to access your company and customer data.
As an I.T. administrator, this presents a challenge of keeping your company's information safe. As you know, with mobile devices, there is an inherent risk that you and your organization is exposed to. If a mobile device is lost or stolen and it is not properly secure, you run a risk of exposing sensitive information to someone with malicious intent. If your company needs to comply with HIPAA, PCI, or some regulatory agency, this risk should concern you greatly.

Misplaced Mobile Devices Leads to HHS Investigations, Millions in Fines
In a February 14, 2017 article written by Tammy Worth at Renal & Urology News, it reported that in 2016, The University of Mississippi Medical Center was fined $2.75 million and the Oregon Health & Science University was fined $2.7 million stemming from missing and unencrypted laptops by Health and Human Services (HHS).HHS a federal agency that enforces, as one of its functions, enforcing the privacy and security rules in the Health Insurance Portability and Accountability Act (HIPAA). Help mitigate this risk for your organization by employing a mobile device policy.
Read the articleCapabilities of Microsoft 365 Mobile Device Management
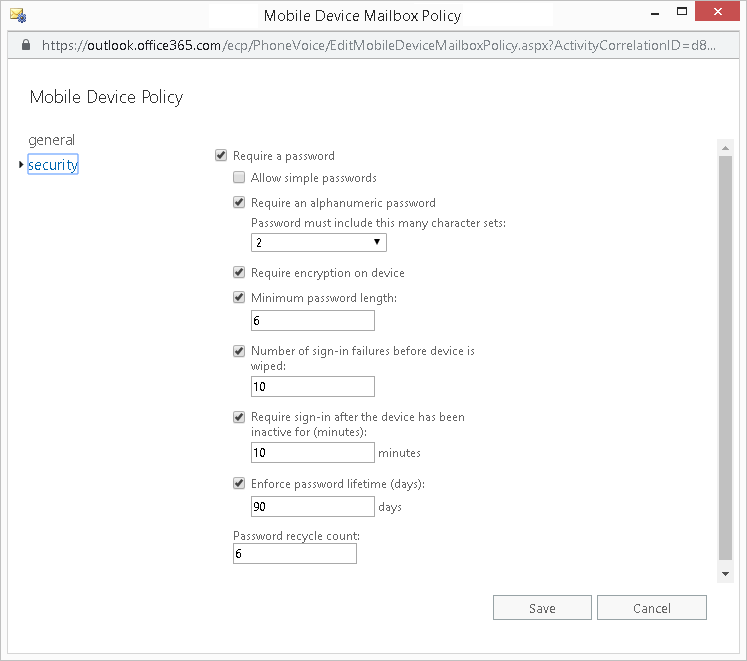
You can help minimize your exposure to this risk by using Microsoft 365 Mobile Device Policy. With this, you are able push out security policies onto mobile devices that connect to your Microsoft 365 environment. Once you security policy is created, you can then applied it to a specific device or set it as the default policy to apply it to all the mobile devices. Some of the configuration settings can define in a policy include:
- Requiring a password for the lock screen
- Define the complexity requirement for the password
- Define the password length
- Defined the number of sign-in failures before the device is automatically wiped
- Ability to require the use of encryption
- Enforce password lifetime
- Password recycle count (password history)
Remotely Wipe a Mobile Device
One powerful capability included with Microsoft 365 MDM that some our the clients value greatly is the ability to remotely wipe a mobile device if it is reported lost or stolen. Some of these clients in particular are in the healthcare industry and are thus required to comply with HIPAA with regardless to protecting personal health information from unauthorized disclosure. If a workforce member loose or misplace their mobile device, the systems administrator logs into Microsoft 365 and with a click of the mouse, the device will be wiped within seconds. Once wiped, your organization's data are delete from the device. We have a separate article that covers remote administrative capabilities that has more information on remotely mobile device wipe. This remote capability, along with a defining a restrict mobile device policy, gives our clients the assurance the risk associated with their workforce use of mobile devices are minimized.

HIPAA Violations and Enforcement
The U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR) is responsible for enforcing HIPAA Privacy and Security Rules. They investigate and investigate complaints, assess compliance, and issue fines and corrective actions in cases where and entity failed to meet compliance to effective safeguard electronic protected health information.
HHS maintains a breach database of HIPAA violations (for cases affecting 500 or more individuals) that is publicly accessible. Although you don't hear it often on the news, privacy violations occur more often than you think.
HHS breach databaseSummary
The use of Microsoft 365 mobile device policies for our clients provide them with an ease-to-use tool to protect company data in the event a mobile device is lost of stolen. For a small business with a small I.T. team, these easy to attain and easy to implement capabilities empowers them with tools for incident response. For organizations that are required to comply with HIPAA, PCI, or any other regulation surrounding the privacy and protection of sensitive customer data, the ability to remotely protect your data from unauthorized disclosure save millions in fines.
Learn more:
- Blog: Remotely Wipe a Device and Delete Data
- Microsoft 365 Mobile Device Management Capabilities
- How to Create and Deploy Device Security Policy on Microsoft 365
- Wipe a Mobile Device in Microsoft 365
- About Microsoft Exchange ActiveSync in Exchange Online
- What is the Health Insurance Portability and Accountability Act (HIPAA)
- Website: U.S. Department of Health and Human Services, Office for Civil Rights
- HIPAA Breach Database - (Breach Portal U.S. Department of HHS, OCR)



