Table of Content
- Overview
- Remote Device Wipe on Microsoft 365
- Remote Notebook Lockdown and Data Delete
- Remote Notebook Lockdown (Device Freeze)
- Remote Notebook Data Delete
- Other Absolute Software Features
- Summary
Overview
Some of the client projects we've worked on had a requirement to enable their systems administrators the capabilities to perform device wipe or data deletion on their workforce mobile devices. More specifically, they have a workforce that use smartphones and notebooks to do their work while at the office or on the road. As an organization that are required to comply with HIPAA, PCI or other regulation, these clients need a way to make sure sensitive information (such as bank account numbers, social security numbers, health claim data and customer names) on mobile devices can be remotely deleted if the device is either lost of stolen.
For the most part, these clients are small organizations that do not have a large budget to purchase or a large I.T. team to administer and maintain a complex solution to satisfy this requirement. To implement a solution that satisfies this requirement at a limited budget, we identify other needs they have to devise a package solution that provided them with the best value. In short, to set up our clients' to remotely wipe data on mobile devices (such as tablets and smartphones) we set them up with a subscription to Microsoft 365 (this solution was used to also satisfy other needs). To be able to remotely delete data from notebooks, we set up our clients with the risk response feature from Absolute Software.

Unencrypted Data on Laptop Results in Huge HIPAA Settlement
In an April 22, 2014 HIPAA Journal article, it reported Concentra Health Services and QCA Health Plan, Inc were both fined close to $2 million together for failing to safeguard electronic protected health information (ePHI). Both had a laptop stolen that contained unencrypted ePHI. Because of the potential HIPAA violation, both were investigated by OCR and found to not be in compliance with HIPAA Privacy and Security Rule regulations.
Help ensure your data is secure by considering many of the useful cyber security information shared in this article and many like it on this website.
Read the HIPAA Journal articleImplementing these two solutions to gain the capability to remotely wipe data from smartphones and notebooks as a tool for incident response may not work you. As the system administrator for your organization, we encourage you to evaluate a solution that best fit your environment. We are here to share our experiences with you and some insight on how remote data deletion looks like on Microsoft 365 and Absolute Software.
Remote Device Wipe on Microsoft 365
Microsoft 365, as many of you already know, offers a plethora of features for business productivity. Depending on the subscription level, Microsoft 365 does offer the ability to remotely wipe a smartphone through Mobile Device Management (MDM). Most will use their smartphone to check and respond to emails, look up information, or other digital content in their Microsoft 365 environment. With MDM, if your staff members ever report to you that their smartphone is either lost or stolen, you can remotely wipe your company's data from the device in seconds.
The remote wipe feature supports popular iOS and Android devices that sync with Microsoft 365 using Exchange ActiveSync. If a device is reported lost or stolen, a system administrator can log into Microsoft 365 admin center web portal, highlight the effected device and perform a remote wipe with a click of the mouse. A screenshot of this provided below. During testing, the automatic wipe on the mobile device happens within several seconds from when the command was triggered. As it is being wiped, the person in possession of the device does not have the ability to abort or cancel the action.
Steps to Perform a Remote Smartphone Data Wipe on Microsoft 365
- Login to your Microsoft 365 admin web portal.
- On the left sidebar, select Admin Centers > Exchange.
- Click Recipients and highlight the user that has the device to be wiped.
- On the right sidebar, click on View Details as highlighted below to open the Mobile Device Details dialog box.
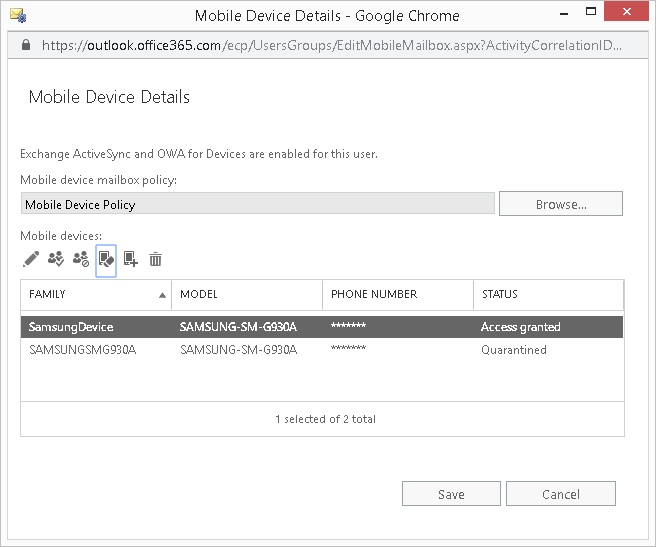
- From the list of mobile devices, highlight the one to be wiped and click on the Wipe Data icon as illustrated below.
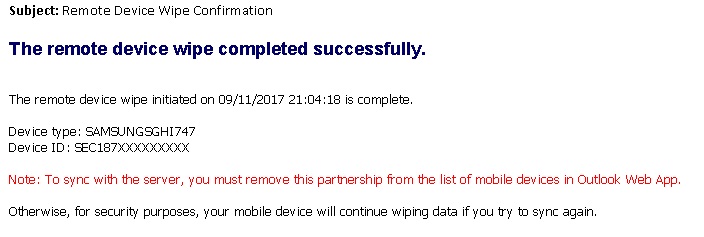
- Within a few seconds, you'll get an on-screen confirmation that the remote wipe succeeded. Additionally, the Microsoft 365 administrator(s) will receive an email confirmation as well, illustrated below. Once the wipe is complete, the mobile device is rendered back to its original out-of-the-box state (e.g., a newly un-configured device).
This remote capability, along with defining a strong mobile device policy, provide a strong security layer around your workforce smartphone. As long as you train your staff to immediately report to you when their device is lost or stolen, as a systems administrator, you'll be able to maintain positive control over your company's data. As mentioned, this remote wipe function on Microsoft 365 is available only on mobile devices that are set up to use Exchange ActiveSync as the communication protocol.
Remote Notebook Lockdown and Data Delete
Implementing a solution for our clients to provide them with the capability to remotely lockdown and delete data off their workforce notebooks is a more involved. We identified the solution from Absolute Software to be option that offer this and other features to best match our project needs. With a subscription service to Absolute Software, a customer has the capability to perform either a device freeze or different levels of data deletes on their workforce notebooks remotely.
How Absolute Software implements this capability is by "baking in" their agent software on to select notebooks. They work with notebook manufacturers such as HP and Dell to embed their firmware onto the select notebook models in a manner that can not be deleted by a user. You can check their BIOS and firmware compatibility list to identify if your notebooks are supported. In addition to remote lockdown and data delete, you have the ability identify the geographical location of a device, audit hardware and software attributes, and even recover lost or stolen notebooks with Absolute Software's investigative services.
Remote Notebook Lockdown (Device Freeze)
Sometimes it is necessary to lockdown a notebook when it is lost or stolen. By performing a remote lockdown with Absolute Software, the notebook is prevented from booting. Instead, when it is powered on, a message (which you compose) is displayed in a DOS-looking screen. Typically the message you want to show is a set of instruction for a person to contact your company and return the lost device.
Steps to Perform a Device Freeze with Absolute Software
- Login to your Absolute Software web portal.
- On the left sidebar, click on the Administration icon.
- Click on Device Freeze > Request Device Freeze.
- Define the parameters of your freeze request as illustrated below.
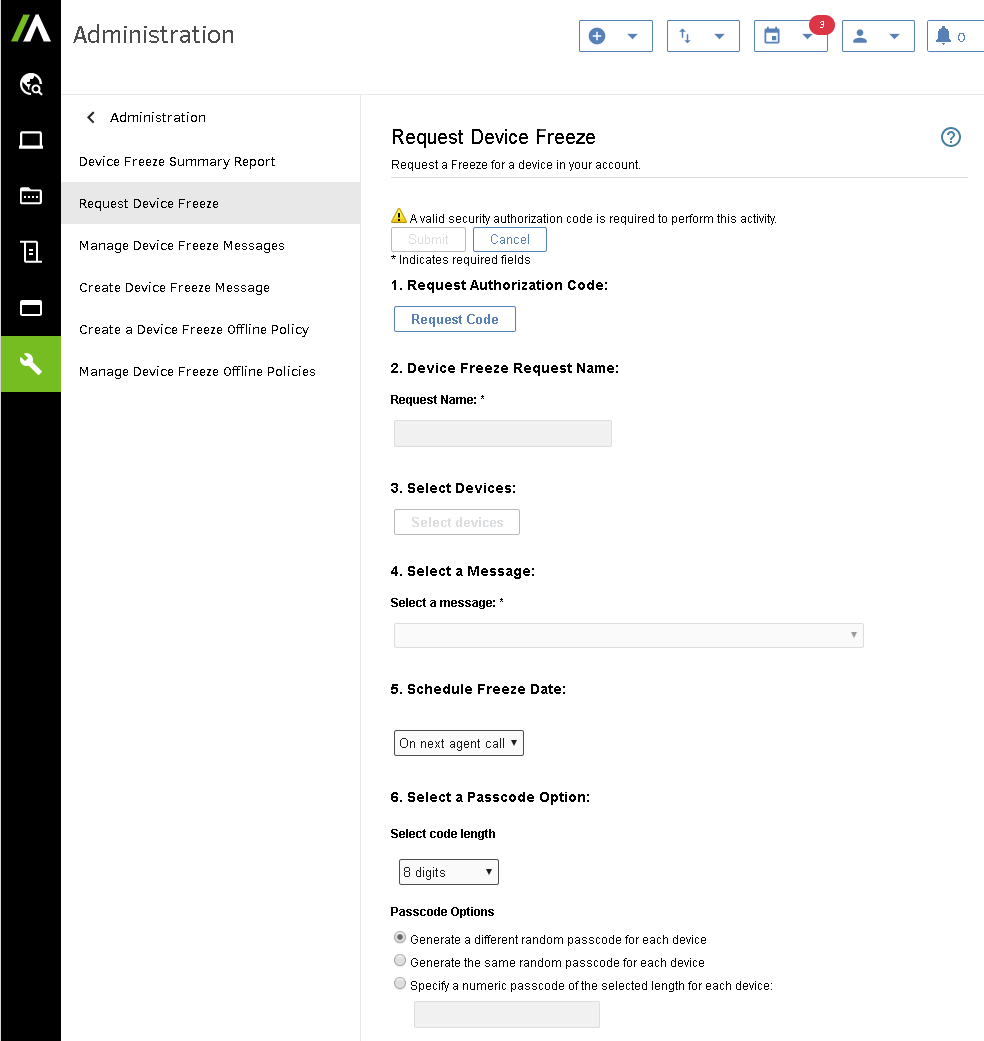
- Click Submit.
From our experience, the amount of time needed to complete a device freeze is approximately 10 minutes to an hour after the agent on the device "calls in." Once the freeze has taken place, an email is sent to you to confirm the action is complete. A screenshot such message is shown below. You do have the option to remotely unfreeze a device if needed.
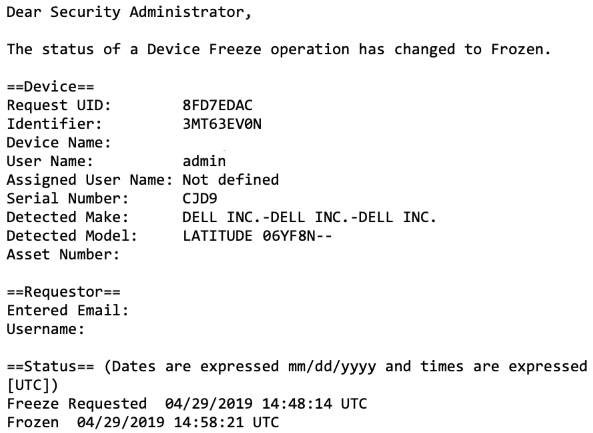
Remote Notebook Data Delete
The Absolute Software remote data delete feature gives you the capability to deny access to sensitive data on your notebook in the event is it lost or stolen. The data delete initiates without prior notice or indicators to the user of the target computer. The user may start noticing files or icons disappearing and eventually seeing the notebook automatically reboot. However, the user will not be able to intervene in the data delete process, even if they attempt to force a reboot mid-way through the process. The pre-installed agent software will continue with the delete process after the reboot. There are a few types of data delete Absolute Software offers. You define the type of delete applicable to you when you submit the delete request.
- Perpetual Data Delete - Continuously perform a data wipe of the hard drive on the target computer. As long as this option is enabled for the target computer, any attempts to reinstall the operating system will be unsuccessful. This option will not be affected in the hard drive on the target computer is replaced.
- Data Delete - Delete specified files from the target computer so is it no longer accessible through the operating system. However, the deleted files can still be recovered with the use of a file recovery software since the hard drive platters still contain the actual content of the "deleted" files. This delete option is transparent to the user of the target computer.
- Data Wipe - Deletes specified files from the target computer and performs a data sanitation on the hard drive itself where those files resided to prevent the files from being recoverable through a file recovery utility software. This delete option is transparent to the user of the target computer.
- End of Life - Perform a data wipe and terminates the agent. However, as per Absolute Software, the hard drive of the target computer must not have encryption (e.g., Bitlocker) and it needs to be hard wired to a network with Internet access. This option is useful if the notebook is being sold or transferred to a new owner.
Steps to Perform a Data Delete with Absolute Software
- Login to your Absolute Software web portal.
- On the left sidebar, click on the Administration icon.
- Click on Data Delete > Request Data Delete
- Define the parameters of your freeze request as illustrated below.
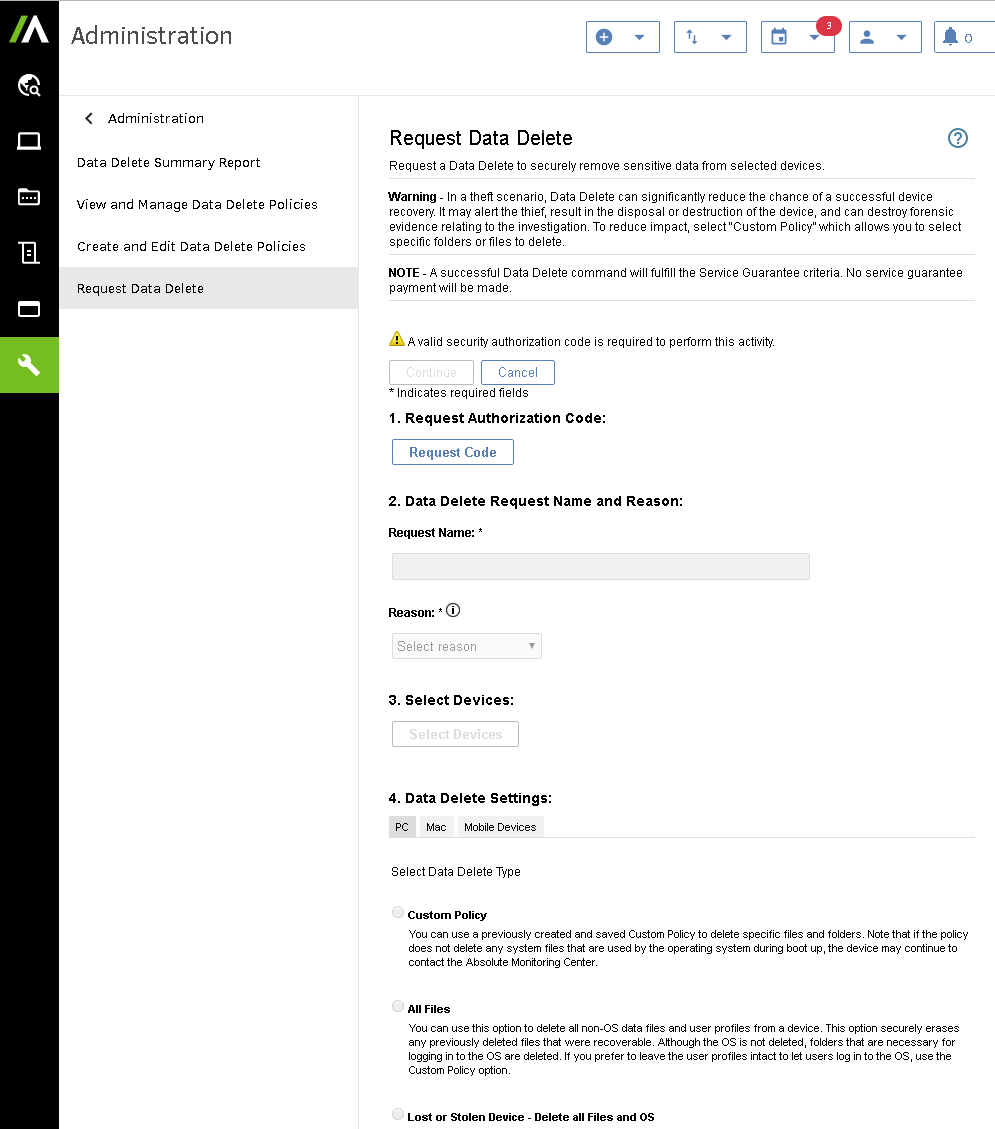
- Click Submit.
Other Absolute Software Features
In addition to the remote device freeze and data delete, there are other tools Absolute Software can provide your organization to help ensure your organizational data are protect. They include, but not limited to:
- Assess hard drive encryption status scan (e.g. Bitlocker)
- Track device location with 365 days of history
- Scan for ePHI and PII data on the device
- Anti-virus status scan
- Software inventory scan
If you have compliance requirements such as HIPAA, Absolute Software tamper-proof solution can provide you capabilities for device tracking and data protection for your endpoints. It is a solution worth exploring if you are in need a cloud-based visibility and control solution.
Summary
The use of Microsoft 365 and Absolute Software for our clients provide them with an ease-to-use tool to protect company data in the event a mobile device is lost of stolen. For a small business with a small I.T. team, these easy to attain and easy to implement capabilities empowers them with tools for incident response. For organizations that are required to comply with HIPAA, PCI, or any other regulation surrounding the privacy and protection of sensitive customer data, the ability to remotely protect your data from unauthorized disclosure save millions in fines.
Learn more:
- Blog: Office 365 Mobile Device Policy
- Microsoft Office 365 Mobile Device Management Capabilities
- How to Create and Deploy Device Security Policy on Office 365
- Wipe a Mobile Device in Office 365
- About Microsoft Exchange ActiveSync in Exchange Online
- Absolute Software Features and Editions
- Absolute Software FAQs
- Absolute Software BIOS and Firmware Compatibility List
- What is the Health Insurance Portability and Accountability Act (HIPAA)
- Website: U.S. Department of Health and Human Services, Office for Civil Rights
- HIPAA Breach Database - (Breach Portal U.S. Department of HHS, OCR)