Table of Content
- Prerequisite
- Overview
- Transport Layer Security (TLS)
- Microsoft 365
- How to Setup an Enforced TLS Connector in Microsoft 365 Exchange Online
- Regular Testing of Secure Email
- Summary
Prerequisite
To implement TLS encryption as described in this article, you will need to have the following:
Prerequisite: Subscription to Microsoft 365
Ease of Implementation: Easy
Cost: None
Time to Implement: <30 minutes
Overview
Email is the most ubiquitous method of communication. Despite that, it is inherently unsecure. Email messages by default traverses the Internet in clear text (unencrypted). This means the content of emails can be viewed by someone it was not intended for. When you send an email, your message can hop through several email servers before reaching the email server of your recipient. By default, email servers do not employ encryption when relaying messages.
For servers that do, it is employed opportunistically. Meaning, when it can it will use encryption. But if it can't (such as when the next hop email server does not support encryption), it will sent it anyway without encryption. From a compliance standpoint, this is not sufficient. Any sensitive data in your email has the potential to be exposed without you knowing about it if encryption is not used..
Transport Layer Security (TLS)
TLS (Transport Layer Security) encryption is a mechanism (also referred to as STARTTLS protocol) used to send or receive emails securely. With this, your message is encrypted as it traverses the Internet to protect your information from eavesdropping.
If your company regularly send and receive sensitive information through email as part of your business function, you will need employ Enforced TLS (also called mandatory, forced or required TLS). Unlike Opportunistic TLS, enforced TLS requires each email server to encrypt your message as it relays it to the hop. Organizations that handle credit card and banking account information, personal health information (PHI) and personally identifiable information PII) are excellent candidates for enforced TLS email encryption.

Email is Unsecure by Default
Email is sent unencrypted (in clear text) through the Internet by default. It was not designed with privacy or security in mind. Unless you specifically employ encryption, sensitive information can be exposed as your message traverse routers, network switches and email servers on its way to your recipient's inbox. If you are in financial industry, healthcare industry, or work with trade secrets or any sensitive that cannot be compromised, you need to enforced TLS encryption.
Microsoft 365
While there are third-party vendors that offer secure email as a service, for our project our client had an existing subscription to Microsoft 365 E3 plan - which included Exchange Online with support for enforced TLS. This client works with a handful of business partners where they need to regularly email sensitive data between each other as part of their business function. We leveraged our clients existing Microsoft 365 subscription to implement secure email.
Microsoft 365 makes it easy to implement enforce TLS. With a few clicks of the mouse, enforce TLS partnership can be quickly established with their vendors. More importantly for our client, it is easy to administer and maintain. With Microsoft 365, there is no need to buy and install security certificates (which some of you may know is not always easy), no specialized training or skill set needed to support this, nor is there a change in the way the end users send emails.
To setup enforced TLS with a vendor, you will need to interact with the other party's systems administrator to have them configure their email server as well. This mutual configuration between two organizations assures all email messages, regardless whether it contains sensitive information or not, are encrypted and sent securely across the Internet. From past experiences, setting up a TLS connector with a business partner typically takes less than 30 minutes.
How to Setup an Enforced TLS Connector in Microsoft 365 Exchange Online
Before setting up a TLS connector, you will need to have the following:
- the domain name (e.g., acmecorporation.com) of the organization you wish to establish enforced TLS with
- a valid email address from that domain (e.g., john@acmecorporation.com)
With Microsoft 365 Exchange Online, the process of setting up enforced TLS is broken up into two steps:
- Create an outbound TLS connector
- Create an inbound TLS connector
Creating an Outbound TLS Connector
- Login to Microsoft 365 as an administrator.
- Click on the waffle icon on the top-left and select Admin to go to the Admin Center.
- On the left sidebar, expand Admin Centers and select Exchange to go to the Exchange Admin Center.
- Click on Mail Flow on the left sidebar, then click on the Connectors tab.
- Click on the plus symbol to add a connector.
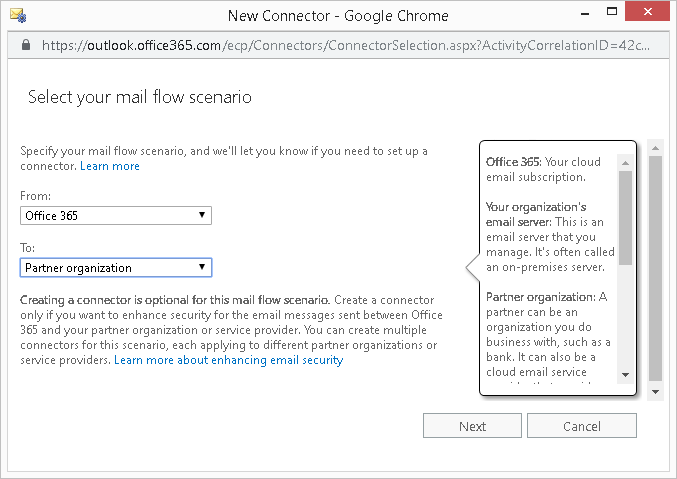
- For the "From" drop-down list,, select Microsoft/Office 365.
- For the "To" drop-down list, select Partner Organization, then click Next.
- In the name field of this outbound connector, type in a descriptive name for it, for example, "To acmecorporation.com."
- Leave the checkbox checked for "Turn it on" and click Next.
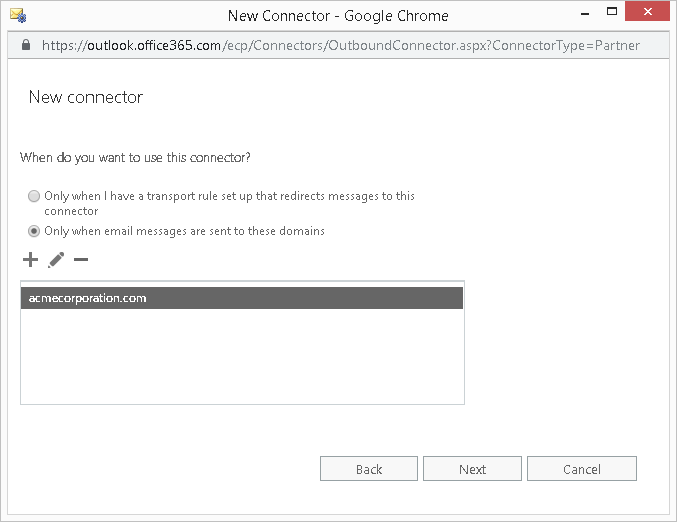
- Select the radio option "Only when email messages are sent to these domains."
- Click on the plus symbol.
- Type in the domain of your vendor in the text box provided and click Ok. You should have a screen that looks similar to the one below.
- Click Next.
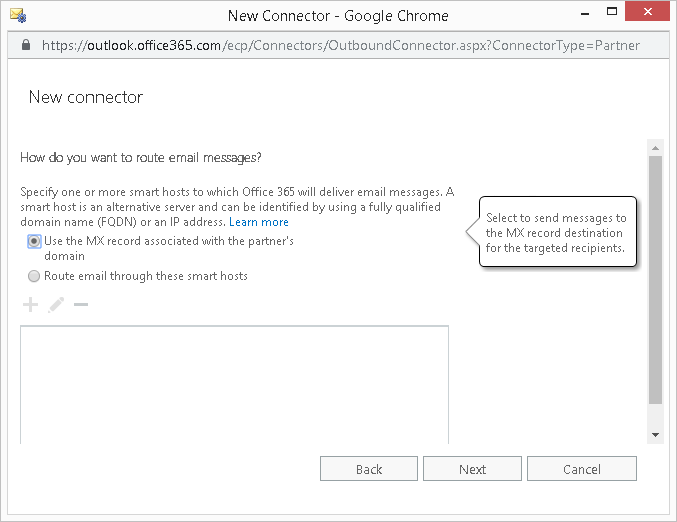
- When prompt about how to route message, select the option "Use the MX record associated with the partner's domain" and click Next. This is the option that typically applies to many of the connectors we were involved in creating. You will need to check if this option applies to the connector you are creating.
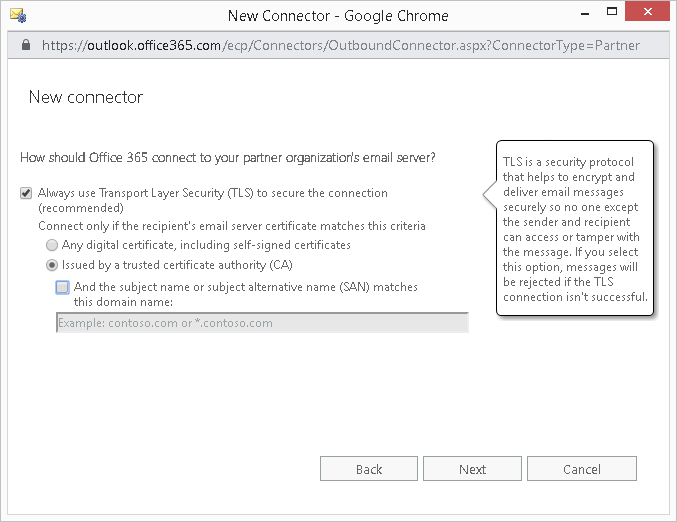
- When prompted for how Microsoft 365 is to connect to your partner's email server, make sure the option for "Always use Transport Layer Security (TLS) to secure the connection" is selected. This is the "enforced" portion of enforced TLS.
- For most setups we've worked on, the default option "Issued by a trusted certificate authority (CA) applies to most.
- Click Next.
- Verify your configuration in the summary dialog box and click Next.
- In the validation dialog box, you will need to enter an email address from your partner domain and click Validate. Microsoft 365 will then perform a check to make sure it is able to establish an enforced TLS connection with the domain's email server. This is accomplished by sending the email address you specified a test message that looks similar to the one illustrated below. There is not action the recipient needs to take in the validation process.
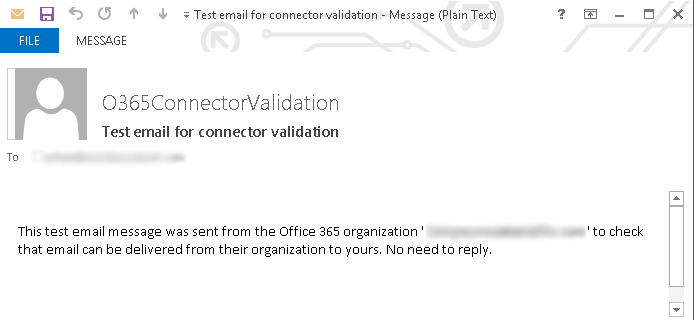
If the connection validates successfully, you will see a message similar to the one shown below.
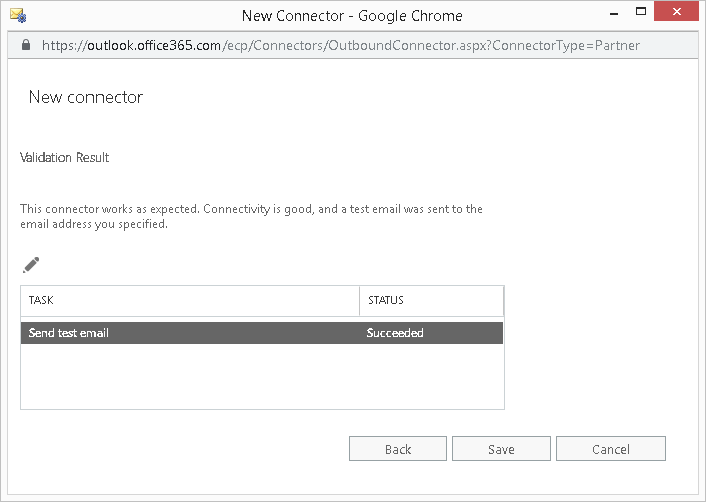
- Click Save and your outbound enforced TLS connector is now successfully created and validated.
Creating an Inbound TLS Connector
- Assuming you are still at the Exchange Admin Center after completing the outbound connector, click on the plus symbol to add a connector.
- For the "From" drop-down list, select Partner Organization.
- For the "To" drop-down list, select Microsoft/Office 365, then click Next.
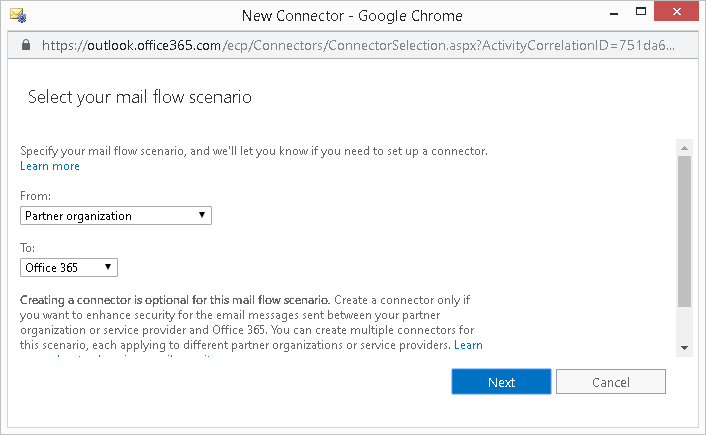
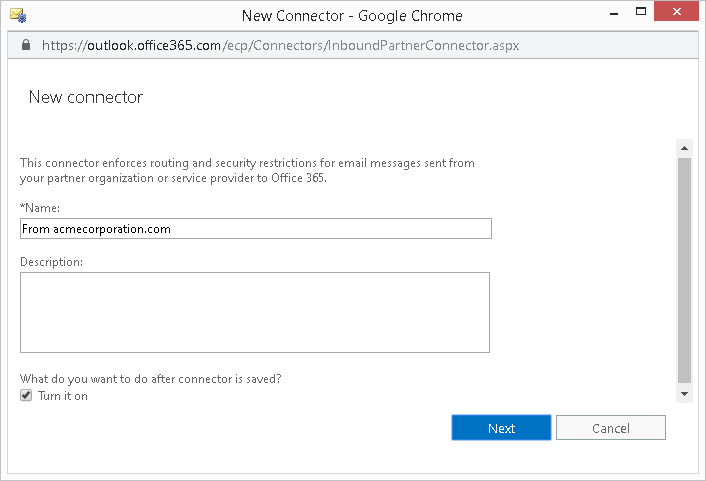
- In the name field of this inbound connector, type in a descriptive name for it, for example, "From acmecorporation.com".
- Leave the checkbox checked for "Turn it on" and click Next.
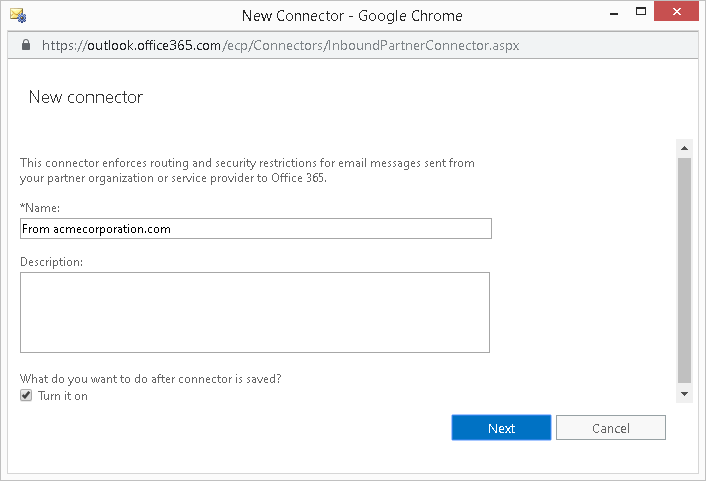
- Select the radio option "Use the sender's domain" and click Next. Alternatively, you can select "User the sender's IP address" if applicable in your implementation.
- Click on the plus symbol.
- Type in the domain of your vendor in the text box provided and click Ok. You should have a screen that looks similar to the one below.
- Click Next.
- Select the checkbox option "Reject email message if they aren't sent over TLS" and click Next.
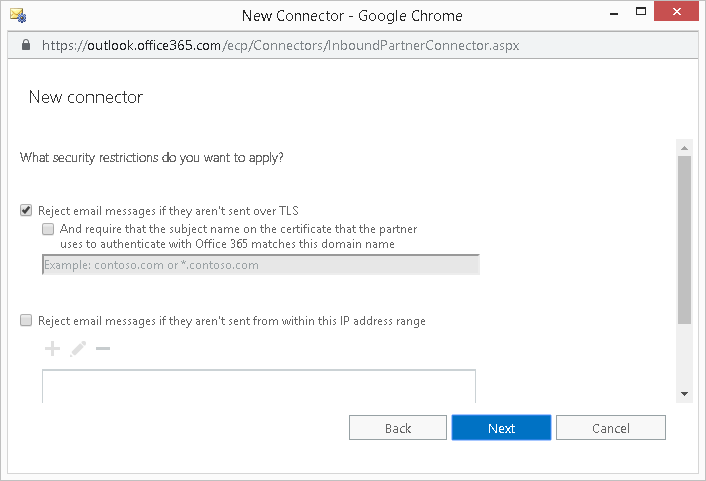
- Verify your configuration in the summary dialog box and click Save. Your inbound enforced TLS connector is now created.
Unlike setting up the outbound TLS connector, there is no way to test the inbound from within the setup wizard. However, you can have your counterpart send you an email and manually inspect the message header. See the section below to learn more.
Regular Testing of Secure Email
As best practice, you should validate your enforced TLS mail flow connectors on a regular basis (at least once a year). This is will help ensure that your business partner's email server is still configured to mandate the use of TLS encryption when your organization sends them emails. You can use the Microsoft 365 validation tool or third-party tools. To learn more, please see the article titled How to Check/Test TLS Encryption is used to Secure Emails.
Summary
For some of our clients, they are mandated to protect customer information in email messages either by policy, regulation or be other means. Microsoft 365 has the feature to satisfy the requirement. It is easy to create connectors and requires little to no administrative effort to maintain. It does require a subscription to Microsoft 365, but if you have one already, enforced TLS is worth exploring further. If you have a small I.T team and don't have a dedicate person or team to implement an on-premise solution, consider Microsoft 365. Even if you do not have an existing subscription, the added cost to do so may be worth it.
Depending on your subscription level, there are other security features (such as two-factor authentication (2FA), mobile device management, safe links and safe attachments) that comes with Microsoft 365 that may help you in other areas to enhance your overall security posture for your organization by a measurable degree.
With Microsoft 365, establishing a persistent secure email connection with business partners is easy and effective. By configuring your Exchange Online, your emails will always be encrypted - inbound and outbound. Best of all, there's no training required for your end users - enforced TLS encryption is transparent.
Learn more:
- What is Transport Layer Security (TLS)?
- How Exchange Online uses TLS to Secure Email Connections in Microsoft 365


