Table of Content
- Overview
- Change the Default Password
- Update the Firmware
- Use HTTPS or SSH When Accessing Control Panel
- Disabling Unnecessary Services and Ports
- Remove or Sanitize Hard Drives Before Disposal
- Deny Access to the Internet
- Output Tray
- Disable Remote Administrative Access
Overview
A common overlooked device on a network when it comes to network security are printers and copiers (which we will collectively call 'printers'). Many printers nowadays, not just business printers but even consumer-level/home printers as well, have network capabilities built-in. A network printer that is not secure can open you up to a cyber attack. Just like computers, there may be vulnerabilities in its firmware that hackers can exploit to break into your network. Or, malware can be installed onto your printer where hackers can access sensitive information. Printers have memory chips and/or hard drives and are thus a potential treasure trove of data for cyber criminals. These easy to implement steps help with enhancing your overall security posture when it comes to network printer security.
Change the Default Password
Most printers offer a web interface to allow administrators to configure the printer. These printers will come out-of-the-box with an often publicly advertised default password. Anyone with the right password can log into the printer's administration interface cause bad things to happen (such as emailing a copy of print jobs to a hacker's mailbox). You want to change the default password before deploying new printers and take the time to change the password on the printer you already have on your network - making sure the password is complex (using uppercase, lowercase, numbers and symbols). This is easy to do and a very effective means to secure your printers.
Update the Firmware
Like any software, bugs and vulnerabilities may be discovered that poses a security risk. Printer manufacturers will provide firmware updates through their website where you can download and update your printers with. You can find the firmware version your printer is currently on by either the web administration interface or on the control panel at the printer itself. Compare your version number to the latest version available by the manufacturer. If the manufacturer has a version number higher than yours, your firmware is out of date.
For many printers, the process of updating the firmware is easy. If you have ever update the firmware of your home router, the experience is similar. You essentially:
- Log into your printer's administration interface.
- Navigate to the firmware update tool.
- Click on the provided "browse" button to find and select the firmware file you downloaded from the manufacturer.
- Then click upgrade.
Typically, the printer will need to restart itself after the update. You can confirm the update was successful by checking the version number now on the printer. If you are afraid of losing your network configurations, output settings and other printer options, you shouldn't be. I don't recall coming across a project where configurations where changed or the printer defaulted to out-of-the-box setting stemming from a firmware upgrade.
Firmware updates aren't frequency. Thus, this isn't something you need to check on a monthly basis. Add it to your semi-annual or annual network to-do list and you'll have this covered.
Use HTTPS or SSH When Accessing Control Panel
As mentioned, many printers offer a web interface for administration purposes. If possible, configure your printer to only allow HTTPS connection to the interface. This will prevent someone on your network from eavesdropping and gathering printer or network information that can be used to launch an attack. For small organizations, this may not be considered a high risk. But if you are an organization with hundreds of users (such as a college), a risk assessment may deem this to be high.
In additional to a web interface, some printers offer the Telnet capability to enable you an alternative means of access to perform administration of it. If your printer support it and you prefer or need command-line access, consider using SSH instead of Telnet since it support encryption.
Disabling Unnecessary Services and Ports
Many printers provide support for many services/protocols as a feature. There may be services that are enabled by default that your organization do not need (such as FTP, faxing). You want to identify the various services enabled on the printer and disabled those you do not need. Having unnecessary services running can provide cyber bad guys the ability to access sensitive information or launch an attack against your network. Turning off services on a printer is often as simple as un-checking a checkbox on the web interface.

Photocopier data breach costs Affinity Health Plan $1.2M
In an August 14, 2013 Healthcare IT News article, it reported that Affinity Health Plan inadvertently disclosed protected health information of approximately 344,579 individuals when they returned multiple leased photocopiers to leasing agents without first erasing the data contained in the internal hard drives. The Health and Human Services (HHS), Office for Civil Rights (OCR) fined Affinity $1.2 million (USD) for violating the HIPAA Privacy and Security Rules.
Help ensure your data is secure by considering many of the useful cyber security information shared in this article and many like it on this website.
Read the Healthcare IT News articleRemove or Sanitize Hard Drives Before Disposal
Some business printers are built with an internal hard drive for the purpose of storing print and scan jobs. When you are ready to dispose of your printer (even if it is going to a electronic recycling center), you want to remove the hard drive. If you are leasing your printers, arrange with your printer vendor during the procurement process to include a clause in your agreement that your company will remove and retain the hard drive before return the printers. The hard drives can then be sent to a data destruction company where they will degauss (and shred) them to wipe any data on them - rendering the data unrecoverable.
Alternatively, some business-class printers offer an optional built-in feature to sanitize the hard drive. This feature will allow you to wipe the hard drive to prevent the recovery of print job data files, even if a file was already deleted. This is typically performed right at the printer's control panel. Once launch, we have seen the sanitization process take 30 minute to a few hours to complete. The amount of time need will vary by manufacturer and by the size of the hard drive.
Deny Access to the Internet
Some printers come with the ability to be configured to access the Internet, such as for the purpose of emailing a scanned document. Unless there is a specific need that cannot be otherwise fulfilled through other established means, you want to block your printers from having access to the Internet. This can be accomplished by configuring your firewall to deny Internet access to your printers - both inbound and outbound. Assign your printers with static IP addresses to facilitate this.
Implementing this will prevent someone from accidentally or intentionally transmitting potentially sensitive information to unauthorized individuals. Although not likely, this will also prevent a compromised printer (e.g., malware infection) from sending potentially sensitive information to a third-party.
Output Tray
A vulnerability that is not so obvious is the printer output tray. Users will print sensitive documents and can forget to pick them or print them to a wrong printer. Even if the user does immediately walk toward the printer to pick up the document, there's still a chance sensitive and privileged information can be viewed by another employee that happens to be walking by the printer at the time. If you are an organization that needs to comply with privacy and security regulations, such as HIPAA and SOX, this potentially is a violation.
There are two typically methods organizations use to address this vulnerability. One is to configure your printer to print a cover sheet for each print job. The other is to employ secure print. The purpose of the cover sheet is to 'cover' the content of the document from unauthorized disclosure. Additionally, the cover sheet may have information about who printed it so that the right person can be identified to take custody of the document.
The cover sheet option is not the ideal as it is not 100% secure. The best option is to use the "secure print" if your printer supports. With this option, when users print a document, they will need to provide a PIN (one that they define themselves) at the printer dialog box before they click on the print button (see screenshot example below). Once the printer receives the print job, it will hold it in queue. The printer will only print the document when the user walks up to the printer and enter their PIN. This way, the user will be physically by the printer to 'guard' the document from unauthorized disclosure.
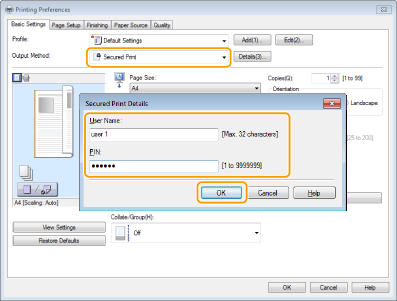
Disable Remote Administrative Access
Sometimes with leased printers, the vendor may want to establish a means to remotely access the printer across the Internet or a telephone line for the purpose of running diagnostics or health monitoring. From a security standpoint, there is a risk to any remote access. Having worked with network printers for decades, we have never come across a situation where allowing a printer vendor remote access served to have mitigated or prevented a concern for our clients. For some, the risk is too high to permit this type of access. For organizations that need to comply with HIPAA, the cost of unauthorized disclosure of customer health data can cost millions.

